IoT security and device discovery
Security and discovery are two major system requirements in Internet of Things. Decentralized peer-to-peer computing could address both. Public/private key cryptography (PPKI) is a natural element of most decentralized systems. PPKI, specifically using the public key allows a simple but robust authentication and identity management on the network.
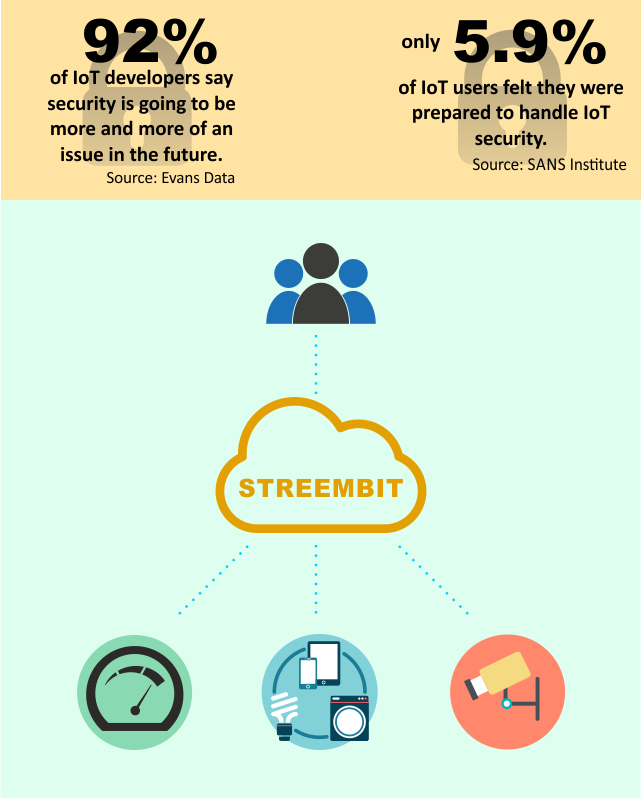
Streembit also utilizes the concept of decentralized, peer-to-peer computing to perform device discovery. In order to communicate, first users/devices must find each other on the Internet enabled networks. A decentralized system manages this tasks without using a centralized system or service. Streembit manages device discovery as well as authentication, access control and provisioning of devices without using a centralized authority server. The system facilitates device discovery and device control in a peer to peer manner. The owners and authorities in the centralized (client-server) topologies all have an influence upon the network and can be exploited. They can ban devices and spy on devices. In fact, government can order them to do any or all of these. Streembit excludes third party service and cloud providers from the ecosystem to give full control to the end users over the devices.
Check out the other open source projects I have contributed. You can contact me at [email protected] if you have any questions or comments.
